Video conferencing within FACETS[]
For video conferences withing the project we are using the H.323 standard compliant video conference systems. Some partners have conference rooms equipped with build in video conferencing equipment and room audio systems from e.g. Tandberg.
Not all project partners have easy access to pre-configured video conferencing rooms. Therefore we are also using the cheap software solutions with existing PCs. We are using:
- As video conference software client the Polycom PVX 8.0.2 software (for PC only) from Polycom
- A webcam (e.g. the Philips SPC900NC Webcam)
- For audio:
- A headset (=no problems with echo)
- or the Polycom Comminicator (having some echo trouble)
- or the DUET USB Speakerphone (Phoenix Audio Technologies)
Firewalls[]
The H.323 video conferencing protocol is not a 'firewall friendly' protocol at all. It uses TCP and UDP portranges and dynamic port number selection during call setup. This requires either an H.323 aware firewall or a hughe hole in the firewall. As both is not an option at some of our places we using a proxy server / VPN setup instead:
- The GNU gatekeeper software is used to provide a proxy for video conference sessions for our partners (=only one IP address to allow traffic to). We are using the proxy since end of 2006 without problems.
- The OpenVPN client / server is going to be used where necessary to create a VPN tunnel using only one TCP port to send the whole H.323 communication to the GNU gatekeeper server. (In test use as of July 2007. Looks promising.)
With this setup the firewall configuration at the partner site only has to allow one outgoing TCP port to the OpenVPN server. The PVX software is then configured to use the private IP of the Gatekeeper machine and thus sends all packets through the VPN tunnel to the gatekeeper.
OpenVPN setup[]
To be able to accommodate multiple end points with one openVPN server process we are using the configuration with client certificates. In this mode every client has a private key and a certificate signed with a secret server key ("certification authority"). The OpenVPN server then checks for every connecting client whether the key has been signed with the certification authority key. The OpenVPN package contains all necessary scripts to create all necessary keys (certification authority key, server and client keys) and certificates and uses the free openSSL package for the crypto (=no additional cost).
During the creation of the client keys one specifies a CN (CommonName) value. The OpenVPN server can then give the connecting clients specific options based on the CN value of the client. Via this method it is possible to assign each defined client a fixed private IP address (OpenVPN documentation regarding client-specific rules). These fixed private IP addresses can then be used in the GnuGK configuration to assign dialing strings to the specific clients.
Server[]
Minimal server configuration (start from the example provided with the OpenVPN server to have the explanations for the options):
port 1194 ;we are using tcp for the tunnel. UDP is faster but firewall admins do not like UDP proto tcp dev tun ;on our system the tun device (created via ; mknod /dev/tun0 c 10 200 ;and then registered for use in the kernel (has to be done at each reboot) via ; modprobe tun ;) has the name /dev/tun0. This name depends on the flavor of the Linux used. dev-node /dev/tun0 ;Path and filename of the key files ca /keys/ca.crt cert /keys/server.crt key /keys/server.key # This file should be kept secret dh /keys/dh2048.pem ;definition of the server address. The server will be reachable at 10.1.1.1 for the clients server 10.1.1.0 255.255.255.0 ifconfig-pool-persist /usr/local/openvpn_conf/ipp.txt ;we are using a per-client-configuration of the IP address client-config-dir /usr/local/openvpn_conf/clientConfigDir keepalive 10 120 ;comp-lzo user nobody group nobody persist-key persist-tun ;logfiles status /var/log/openvpn-status.log log /var/log/openvpn.log verb 4
Client[]
For each client there is a file with the CN (CommonName, defined when creating the client key) in the defined client-config-dir. Example:
ifconfig-push 10.1.1.6 10.1.1.5
(Note: If the client is a windows system not all addresses are allowed. The documentation lists the allowed combinations). With this setup line the client will have the address 10.1.1.6. This address can then be used in the GnuGK configuration file (see below).
On the client (here: a windows machine) this minimal client configuration is sufficient (again use the example files provided with OpenVPN to get additional info). Our OpenVPN uses the standard port 1194:
client dev tun proto tcp remote ADDRESS_OF_YOUR_SERVER 1194 resolv-retry infinite # Most clients don't need to bind to # a specific local port number. nobind # Try to preserve some state across restarts. persist-key persist-tun #paths to the certification authority certificate and the client key and # client key certificate. These files can be created with the scripts # in the easy-rsa directory installed with the OpenVPN installation ca ca.crt cert client_bk.crt key client_bk.key # Enable compression on the VPN link. # Don't enable this unless it is also # enabled in the server config file. ;comp-lzo # Set log file verbosity. verb 3
In addition to the configuration file the client also needs the ca.crt, client.key and client.crt (=certificate of the certification authority, its own secret key file and the certificate for that key. All these files can be created with the scripts provided by the OpenVPN installation.
To start the tunnel on the windows system just call it from the command line (or a batch file):
openvpn.exe Name_of_the_configuration_file
GnuGK configuration to run as a proxy server[]
;; A proxy gatekeeper is usually register with a parent gatekeeper as a ;; gateway. See child.ini for the configuration. ;; [Gatekeeper::Main] Fortytwo=42 TimeToLive=600 Name=A_NAME ;;Test: try to get rid of a problem which could be related to a broadcast listener UseBroadcastListener=0 UnicastRasPort=1719 [RasSrv::Neighbors] ;;Country Gatekeeper for Germany at the DFN CountryGK=194.95.240.3:1719;0 ;plus additional gatekeepers [LogFile] Rotate=Daily RotateTime=23:00 [RoutedMode] GKRouted=1 H245Routed=0 CallSignalPort=1503 CallSignalHandlerNumber=2 RemoveH245AddressOnTunneling=1 DropCallsByReleaseComplete=1 SupportNATedEndpoints=1 Q931PortRange=30000-39999 H245PortRange=40000-49999 [Proxy] Enable=1 T120PortRange=50000-59999 RTPPortRange=50000-59999 ;It is necessary to define the InternalNework(s). For connections between the internal network(s) and the WAN ; gnugk will act as proxy, i.e. all communication is sent via the gatekeeper proxy. Therefore only ; one access needs to be allowed for the H.323 protocol ports (UDP and TCP on a-lot-of-ports). This ; makes the configuration of the firewall rules much cleaner InternalNetwork=1.2.3.0/24,10.1.1.0/24 [Gatekeeper::Auth] ;This selects that only defined IP addresses can contact the gatekeeper FileIPAuth=required;RRQ,LRQ,Setup [FileIPAuth] ;allow your own network range 1.2.3.0/24=allow ;added for the OpenVPN tunnel. Assuming here that the OpenVPN addresses are in 10.1.1.0 network 10.1.1.0/24=allow any=reject [GkStatus::Auth] rule=explicit ;allow access to the monitor port only from the machine itself 127.0.0.1=1 [RasSrv::PermanentEndpoints] ;define here the endpoints and the dialing strings (similar to phone numbers) ;Example numbers. Use you own numbers in your setup. Your own telephone number is a good choice 10.1.1.6=00496221540000001,FACETS_client_1 ;define addtional clients ; EOF
PVX client[]
In the polycom PVX client then tell it to use the VPN and to use your proxy server:
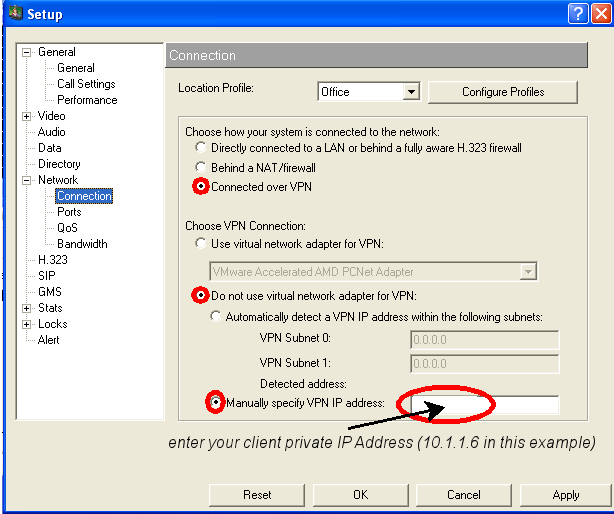
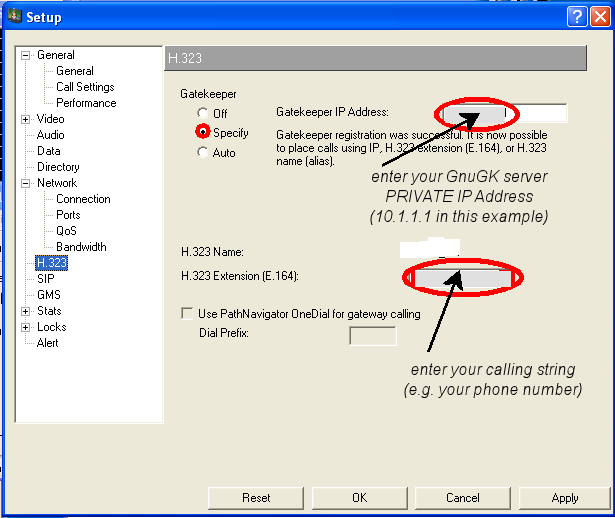
(The H.323 name must match the setting in the gnugk configuration file for this client (i.e. calling string(=H.323 Extension), IP Address and name entered in that configuration file must be echoed in the PVX configuration. The H.323 name can not be edited on this page of the PVX configuration. It is the username selected on the General page of the configuration.)
Multipoint video conferences[]
With the PVX software alone one can run only point-to-point video conferences. For conferences with more that two participants one needs a Multipoint Control Unit (MCU). Most professional video conference systems can act as an MCU system for usually up to 4 participants. For larger conferences a standalone MCU, e.g. from Codian, needs to be used. The drawback is that these units are expensive and most of the time idle if used by a small project. Therefore we are using (and recommend) the Video Conference Service of the German Research Network (the service is only available for DFN members).